Table of Contents
01
Getting Started with HITRUST & What to Expect the First Year
02
Understanding HITRUST Certification
03
What’s the Difference between HIPAA and HITRUST?
04
Three HITRUST Certifications
05
Benefits of HITRUST Certification
06
Your First Year of HITRUST Certification
07
Submitting for and Maintaining HITRUST Certification
08
Secure Sensitive Data and Grow Your Business
Introduction
Digital health startups play an increasingly critical role in healthcare, building solutions that improve the efficiency and quality of healthcare and others that prevent diseases and improve patient outcomes. These digital health solutions frequently require the collection and analysis of significant quantities of sensitive data, particularly protected health information (PHI), which means that putting robust security and privacy controls in place is critical.
The Health Information Trust Alliance (HITRUST) is an organization that developed the HITRUST Common Security Framework (CSF), a comprehensive security and privacy framework for organizations to demonstrate a commitment to compliance, risk management, and protecting and handling sensitive data. The HITRUST certification helps your organization show that you proactively manage security risks and comply with industry standards and leading practices for information security.
02. Understanding HITRUST Certification
HITRUST certification is frequently sought after by organizations in the healthcare industry, although it applies to other related industries as well. The HITRUST CSF is a set of controls and guidelines organizations can use to evaluate and improve their security posture. The CSF provides a framework for organizations to assess their security risks, implement appropriate controls, and measure their effectiveness.
Why Digital Health Startups
Need HITRUST
Most digital health startups are built on collecting and processing data. Lots of data, much of it highly sensitive health information. Working with so much data makes it essential to not only protect it but to prove that you are doing so. HITRUST provides a standardized and auditable framework for protecting data enabling you to provide clear evidence that your business is addressing relevant security practices.
This widely recognized security framework is frequently preferred by hospitals, insurance plans, and other healthcare organizations because the HITRUST CSF is robust, flexible, and regularly updated to keep pace with evolving cyber threats and new regulatory requirements. It brings many existing security frameworks, standards, and regulations together to cover a wide spectrum of security controls, providing a comprehensive, consistent approach to data protection.
A few regulations of particular relevance include:
HIPAA
The federal Health Insurance Portability and Accountability Act of 1996 (HIPAA), a US law which outlines how patient healthcare information can be stored, used, and disseminated, providing civil and criminal penalties for violations.
HITECH
The Health Information Technology for Economic and Clinical Health (HITECH) Act, signed into law February 2009, mandates audits of healthcare providers to ensure compliance with the privacy and security requirements in HIPAA in the US.
GDPR
The European Union’s General Data Protection Regulation (GDPR), put into effect in 2018, requires organizations to safeguard personal data and uphold the privacy rights of any EU citizen’s data and empowers data protection authorities to enforce GDPR with sanctions and significant fines.
HIPAA
The federal Health Insurance Portability and Accountability Act of 1996 (HIPAA), a US law which outlines how patient healthcare information can be stored, used, and disseminated, providing civil and criminal penalties for violations.
HITECH
The Health Information Technology for Economic and Clinical Health (HITECH) Act, signed into law February 2009, mandates audits of healthcare providers to ensure compliance with the privacy and security requirements in HIPAA in the US.
GDPR
The European Union’s General Data Protection Regulation (GDPR), put into effect in 2018, requires organizations to safeguard personal data and uphold the privacy rights of any EU citizen’s data and empowers data protection authorities to enforce GDPR with sanctions and significant fines.
Many other countries, states, and cities have their own regulations regarding the use and processing of personal data, and keeping up to date with all of them can be quite challenging. A HITRUST certification can simplify the compliance process and assure stakeholders that the organization meets all of the necessary regulatory requirements.
There are also many ethical concerns about privacy rights, particularly as more people share their personal data with applications and services in the cloud. Healthcare breaches continue to make the news, increasing the concerns of individuals that their health data could be stolen and used for identity fraud or to discriminate against them. For example, insurance companies could use personal information to deny coverage to people with certain health conditions.
Personal information can also be used to invade individual privacy, allowing advertisers to target people and track an individual’s online activity. Individuals, understandably, want to know that their private and sensitive data is protected. Similarly, governments, payors (such as insurance companies), and healthcare providers also want to ensure the entities they do business with are committed to protecting the data they collect and analyze. Digital health startups must adhere to a wide range of regulations even as they leverage sensitive data to improve healthcare outcomes. Adopting and complying with rigorous frameworks, such as HITRUST, can help you ensure that you protect this essential data.
03. What’s the Difference between HIPAA and HITRUST?
HIPAA is a federal regulation, while HITRUST is a voluntary third-party certification. There are some similarities and overlapping controls between HIPAA and HITRUST, especially related to the controls of sensitive information. Both HIPAA and HITRUST outline requirements for the protection of sensitive information but differ in how organizations gain assurance.
HIPAA
HIPAA sets standards for covered entities, including healthcare providers, health plans, and healthcare clearinghouses. The U.S. Department of Health and Human Services (HHS) enforces HIPAA through the Office for Civil Rights (OCR) and by the Attorney Generals from each state. Covered entities must comply with HIPAA, and non-compliance can result in fines and legal action. Keep in mind that a service provider to a covered entity becomes a “Business Associate” if the service provider provides services to a covered entity that involves the use or disclosure of protected health information.
A business associate is an organization that receives, maintains, creates, or transmits protected health information on behalf of a covered entity.
There is no formal HIPAA certification, nor is there an accepted standard for external audit reports. HIPAA compliance has a lower level of rigor than HITRUST and is not updated as frequently. Under HIPAA, organizations typically pursue assurance through a Business Associate Agreement (BAA), an assessment report, or a SOC 2+ report. A BAA is a legally binding contract between a healthcare organization and a business associate that outlines the responsibilities and obligations of both parties when it comes to protecting patient data. An assessment report provides a detailed evaluation of an organization’s compliance with HIPAA regulations. A SOC 2+ report analyzes an organization’s controls using the audit guidance published by the American Institute for Public Accountants (AICPA).
HITRUST
HITRUST is a privately held company with not-for-profit divisions, HITRUST Services Corp. and HITRUST Alliance, that collaborated with healthcare, technology, and information security leaders to establish a Common Security Framework (CSF) for organizations to demonstrate to customers, partners, and regulators that they meet key healthcare regulations and requirements for protecting and securing sensitive private healthcare information. While HIPAA assessments allow assessors to use professional judgment, HITRUST offers a certifiable framework with the same level of assurance, regardless of judgment.
The HITRUST organization issues the certification. The HITRUST CSF incorporates nearly 2,000 available controls into a single certifiable framework and updates methodologies, programs, and solutions to stay up to date with complex IT infrastructures, changing regulations, and evolving cyber threats. HITRUST Authorized Assessors go through almost 150 automated quality checks and five levels of independent quality review by Assurance Analysts on HITRUST’s Assurance team to maintain consistency in the assessment, ensure the assessors are competent, and adhere to rigorous standards.
How HITRUST Helps
HITRUST is based on the International Organization for Standardization (ISO) / International Electrotechnical Commission (IEC) 27001:2005 and 27002:2005 and incorporates dozens of additional security and privacy related standards, frameworks, and regulations. It’s a customizable framework that allows you to adjust your security and privacy control baselines based on your organization’s type, size, systems, regulatory, and compliance requirements. There are three levels of requirements defined based on your organization’s system and risk factors (more on that in the next chapter). Each higher level encompasses all the requirements of the lower level to match the increasing levels of risk.
Authorized HITRUST External Assessor Requirements
There are also extensive requirements to become an authorized HITRUST assessor. Assessors must follow agreed-upon procedures to ensure that your organization’s security controls meet the requirements, and assessors must provide a roadmap for you to improve your security posture. These rigorous standards and requirements provide assurance that you meet security standards. They also ensure consistent quality for all organizations attaining HITRUST certification, regardless of the assessor. Importantly, HITRUST reduces the risk that unauthorized individuals or entities will gain access to confidential or sensitive information your organization collects, stores, analyzes, or hosts.
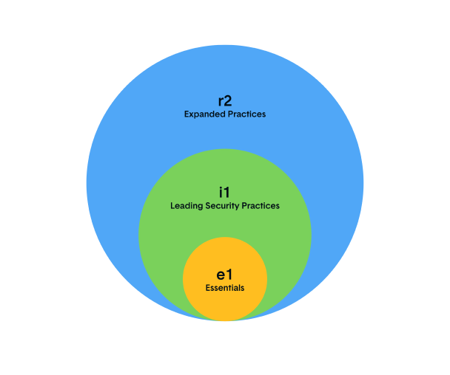
04. Three HITRUST Assessments
The HITRUST Certification includes three types of assessment, each with unique requirements and timelines. The following explains each one to help you decide how to get started.
HITRUST Essentials, 1-Year (e1) Assessment
The HITRUST e1 Assessment is the newest assessment and covers basic foundational cybersecurity practices. These practices address the assurance needs of lower-risk organizations. The e1 includes 44 HITRUST CSF requirements for year one and year two. This new option is faster and more streamlined and acts as a reliable way to demonstrate that low-risk organizations have foundational cybersecurity in place.
The e1 also helps establish benchmarks for cybersecurity, identify coverage gaps, and functions as a way to get meaningful assurance reports for new business units, merger and acquisition partners, or for recently deployed technology platforms. In addition, the e1 can become a first step before moving on to the other assessments.
Aligned to Authoritative Sources: CISA Cyber Essentials Health Industry Cybersecurity Practices for Small Healthcare Organizations, NIST 171’s Basic Requirements, NIST IR 7621
Year 1 requirements: 44
Year 2 requirements: 44
Level of assurance: Low
HITRUST Implemented, 1-Year (i1) Validated Assessment
The HITRUST i1 Assessment provides reliable measurements and moderate assurance against a broader set of cybersecurity controls than the e1. The i1 includes 182 HITRUST CSF requirements for year one and about 60 additional requirements in year two (with rapid recertification).
This certification protects against both current and emerging threats and can help you meet both contractual and compliance obligations. It can help you ensure that your business partners use appropriate security practices to protect information reliably and establish a meaningful benchmark for third-party service providers. It can also provide you with a certification while your organization works on an r2 assessment, functioning as a stepping stone to the next level of assessment.
Aligned to Authoritative Sources: Health Industry Cybersecurity Practices for Medium-Sized Organizations, HIPAA Security Rule, and NIST SP 800-171 (Basic and Derived Requirements)
Year 1 requirements: 182
Year 2 requirements: 60
Level of assurance: Medium
HITRUST Risk-based, 2-Year (r2) Validated Assessment
The HITRUST r2 Assessment is the most stringent of the three assessments. It entails rigorous control requirements, in-depth review, and consistent oversight to provide what is considered the gold standard for information protection assurances. The r2 includes approximately 375 HITRUST CSF requirements for year one (on average) and about 8-100 additional requirements in year two, depending on a variety of factors. It includes thorough policy and procedure consideration, while the other two assessments do not.
The r2 offers risk-based control selection that is flexible and can be tailored to help organizations meet the most stringent risk and compliance factors, offering assurances over specific authoritative sources or international requirements. This certification is appropriate for organizations processing significant amounts of sensitive data and personal information. It allows organizations to assess once but report compliance information as needed, such as for a NIST Scorecard Report or by compiling HIPAA compliance evidence automatically.
Aligned to Authoritative Sources: NIST SP 800-53, HIPAA, FedRAMP, NIST CSF, PCI DSS, GDPR, and dozens of others
Year 1 requirements: 375
Year 2 requirements: 8-100
Level of assurance: High
HITRUST Essentials, 1-Year (e1) Assessment
The HITRUST e1 Assessment is the newest assessment and covers basic foundational cybersecurity practices. These practices address the assurance needs of lower-risk organizations. The e1 includes 44 HITRUST CSF requirements for year one and year two. This new option is faster and more streamlined and acts as a reliable way to demonstrate that low-risk organizations have foundational cybersecurity in place.
The e1 also helps establish benchmarks for cybersecurity, identify coverage gaps, and functions as a way to get meaningful assurance reports for new business units, merger and acquisition partners, or for recently deployed technology platforms. In addition, the e1 can become a first step before moving on to the other assessments.
Aligned to Authoritative Sources: CISA Cyber Essentials Health Industry Cybersecurity Practices for Small Healthcare Organizations, NIST 171’s Basic Requirements, NIST IR 7621
Year 1 requirements: 44
Year 2 requirements: 44
Level of assurance: Low
HITRUST Implemented, 1-Year (i1) Validated Assessment
The HITRUST i1 Assessment provides reliable measurements and moderate assurance against a broader set of cybersecurity controls than the e1. The i1 includes 182 HITRUST CSF requirements for year one and about 60 additional requirements in year two (with rapid recertification).
This certification protects against both current and emerging threats and can help you meet both contractual and compliance obligations. It can help you ensure that your business partners use appropriate security practices to protect information reliably and establish a meaningful benchmark for third-party service providers. It can also provide you with a certification while your organization works on an r2 assessment, functioning as a stepping stone to the next level of assessment.
Aligned to Authoritative Sources: Health Industry Cybersecurity Practices for Medium-Sized Organizations, HIPAA Security Rule, and NIST SP 800-171 (Basic and Derived Requirements)
Year 1 requirements: 182
Year 2 requirements: 60
Level of assurance: Medium
HITRUST Risk-based, 2-Year (r2) Validated Assessment
The HITRUST r2 Assessment is the most stringent of the three assessments. It entails rigorous control requirements, in-depth review, and consistent oversight to provide what is considered the gold standard for information protection assurances. The r2 includes approximately 375 HITRUST CSF requirements for year one (on average) and about 8-100 additional requirements in year two, depending on a variety of factors. It includes thorough policy and procedure consideration, while the other two assessments do not.
The r2 offers risk-based control selection that is flexible and can be tailored to help organizations meet the most stringent risk and compliance factors, offering assurances over specific authoritative sources or international requirements. This certification is appropriate for organizations processing significant amounts of sensitive data and personal information. It allows organizations to assess once but report compliance information as needed, such as for a NIST Scorecard Report or by compiling HIPAA compliance evidence automatically.
Aligned to Authoritative Sources: NIST SP 800-53, HIPAA, FedRAMP, NIST CSF, PCI DSS, GDPR, and dozens of others
Year 1 requirements: 375
Year 2 requirements: 8-100
Level of assurance: High
Which Certification Is Right for You?
Getting your HITRUST CSF Validation with certification can help you gain a competitive advantage. However, because there are multiple HITRUST certification pathways, it can be difficult to choose the right one for your business.
For digital health organizations, HITRUST certification can help you expand and grow your business because it offers a high level of assurance. The e1 certification offers a faster and more streamlined certification process than the other assessments, effectively meeting the needs of lower-risk organizations. The i1 is the best option for the majority of digital health companies seeking HITRUST because it enables your organization to adopt and maintain compliance with requirements for the security of sensitive health information. The i1 also prepares companies well for achieving r2 certification in the future. As an internationally recognized and respected framework, HITRUST can help demonstrate your commitment to essential security controls to your supply chain and internal stakeholders.
While HITRUST certification does require time and effort when it comes to preparing for the assessment and submitting for certification, it can also generate a positive return on investment for your business. Many healthcare systems and insurance providers already require HITRUST certification for digital health organizations, particularly population health contracts. Others recognize the value of the certification because it specifically addresses the needs of healthcare companies. This can help your organization win business against competitors that lack the certification and reduce the likelihood of loss because your organization already mitigated the risks of unauthorized disclosures. By demonstrating a commitment to a healthcare industry standard for data security and privacy, your organization can also increase its validation and improve its marketability if or when your organization considers an acquisition or funding round.
Who gets certified?
While HITRUST certification is not required under law, it is common at digital health organizations that collect, process, and store sensitive health information. These types of organizations must have a comprehensive information security program in place that meets the requirements of leading industry standards, regardless of whether they are certified. Here are a few examples of health organization types that might want to consider pursuing HITRUST certification:
Population Health Management (PHM)
Population Health Management (PHM)
Population Health Management (PHM) organizations collect and store a significant amount of sensitive patient data, including medical history, diagnoses, and treatment plans.
Clinical Decision Support Software
Clinical Decision Support Software
Clinical Decision Support Software companies offer software that doctors use to help make decisions.
Revenue Integrity
Revenue Integrity
Revenue Integrity companies collect, process, and analyze substantial amounts of sensitive data, including patient health information, financial data, and payer information, which is critical for ensuring the accuracy and completeness of revenue cycle management.
Telehealth Providers
Telehealth Providers
Telehealth Providers collect, process, and transmit sensitive PHI over electronic networks.
Value-Based Care (VBC) Providers
Value-Based Care (VBC) Providers
Value-Based Care (VBC) Providers must be able to demonstrate that they have implemented appropriate security controls to protect patient data.
Clinical Research
Clinical Research
Clinical Research involves the collection, analysis, and interpretation of sensitive and confidential data from human subjects.
Health Data Aggregators (HDAs)
Health Data Aggregators (HDAs)
Health Data Aggregators (HDAs) and Health Information Exchanges (HIEs) collect and store vast amounts of sensitive patient data from a variety of sources to improve the quality of care, lower costs, and make healthcare more efficient.
Cloud Hosting Providers
Cloud Hosting Providers
Cloud Hosting Providers must protect sensitive data in the cloud, particularly if they serve regulated industries, such as healthcare, finance, and government.
Health Systems
Health Systems
Health Systems must meet the specific security and compliance requirements of the healthcare industry. HIPAA requires health systems to implement specific administrative, physical, and technical safeguards to protect the confidentiality, integrity, and availability of electronic protected health information.
Insurance Plans
Insurance Plans
Insurance Plans handle a significant amount of sensitive information, including their clients’ personal and financial information. They must also meet the specific security and compliance requirements of the insurance industry.
Increasingly, insurance companies require organizations they work with to become HITRUST certified. Already, United Health, Optum Group, and Blue Cross Blue Shield (BCBS) affiliated plans want their third-party vendors to comply with HITRUST requirements now and in the future. Regulators, including the state of Texas and the OCR, want to see HITRUST certification as it shows a commitment to improving security posture and reduces the risk of data breaches.
Similarly, health systems, including the University of Pittsburgh Medical Center (UPMC), Mercy Health, Ascension Health, and Ardent Health, want all the third parties they work with to comply with HITRUST. Given the sensitive nature of the information they hold and the value it poses to cyber attackers, many more payers, providers, and government entities ask for HITRUST certification.
06. Your First Year of HITRUST Certification
Achieving HITRUST certification is a multi-step process that requires an investment of time and resources. Here are the general steps you'll need to follow:
Determine your readiness
Prior to beginning the certification process, you'll need to assess your organization's readiness for HITRUST certification. This requires you to evaluate your current security controls and identify any gaps or deficiencies.
Select an Approved Assessor
HITRUST requires organizations to work with a HITRUST-approved External Assessor to complete the certification process. The assessor guides you through the process and helps you meet all the necessary requirements.
Complete a Self-Assessment
The HITRUST CSF requires organizations to complete a self-assessment to identify their current security posture and determine what additional controls are needed.
Remediate Any Gaps
Based on the results of the self-assessment, you'll need to implement additional security controls to address gaps in your security posture.
Perform a Validated Assessment
After implementing additional security controls, you must perform a Validated Assessment. This involves a thorough evaluation of your security controls to ensure that they meet the requirements of the HITRUST CSF. Organizations must demonstrate compliance for 90 days prior to the beginning of the audit.
Submit Your Assessment
Once your assessment is complete, you'll need to submit it to HITRUST for review. HITRUST will then review your assessment and determine whether you meet the requirements for HITRUST certification. If you are found to be in compliance with the HITRUST CSF, you will be certified. Your certification is valid for one year starting from the date of submission.
The HITRUST certification process can take several months to complete, depending on the certification level and your organization’s current security posture. A qualified External Assessor can help you understand the HITRUST CSF, assess the current security posture of your organization, and help you with gap remediation.
Traditional Process
The traditional process for becoming HITRUST certified is manual. It begins with a readiness assessment, followed by a report, remediation of the findings from the initial assessment, and another report with updated findings. This is a multi-step process, which requires a contract for each step as well as a new Statement of Work (SOW). This is followed by a Validated Assessment, another report, and finally submission to MyCSF for certification. It involves three separate engagements, even when using the same assessor for each stage.
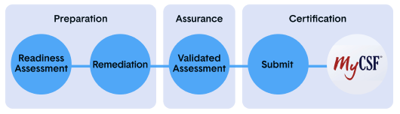
SaaS & Services Process
Another option is software-enabled compliance with accompanying services to accelerate the process. This method includes templates for memos, risk assessments, and business continuity plans. It involves a single contract and approaches the entire process holistically. Using the SaaS and services method eliminates the repetitive steps in the manual process. If you choose to go this route, when reviewing your options, it’s critical to ensure the assessment is done by an approved External Assessor. For successful certification, an Approved Assessor must review the content and submit it to HITRUST with a recommendation. Additional benefits of using software-enabled compliance include:
- Automated evidence gathering
- Customized action items based on findings
- Programmatic verification
- Minimal clerical and communication overhead
The services component also provides expert guidance for your organization in areas where your organization may have knowledge gaps.

How Thoropass can help
Thoropass is the first automated compliance solution to be an approved HITRUST External Assessor. With the HITRUST Validated Assessment and Certification, you’ll receive expert guidance through every step of the HITRUST certification process and be able to manage everything from one easy-to-use platform. Learn more about how you can achieve your HITRUST certification in half the time and with as little disruption to your team as possible.
07. Submitting for and Maintaining HITRUST Certification
To get certified, your organization may start with a self-assessment against the HITRUST CSF to identify gaps in your security posture and address them. An External Assessor must conduct a validation assessment to verify that your organization has implemented the relevant controls in alignment with the level of certification.
Once the validated assessment is sent to HITRUST via MyCSF, you must submit the report to HITRUST and defend the audit. HITRUST reviews the audit and issues the certification if you have achieved everything required. The HITRUST CSF Assurance Program requires organizations to maintain their certification through ongoing compliance with the HITRUST CSF, which includes the following:
An Annual Assessment
HITRUST requires an annual assessment by an Approved Asessor to ensure that your organization's controls and policies are still in compliance with the framework.
Remediation of Findings
Any issues or vulnerabilities identified during that annual assessment must be addressed and remediated in accordance with the HITRUST requirements.
Training and Awareness
Employees and contractors with access to sensitive data must participate in regular training and awareness programs to maintain an understanding of their responsibilities and obligations.
Incident Response Planning
HITRUST requires organizations to have an incident response plan in place that is tested periodically for effectiveness.
Continuous Monitoring
HITRUST requires ongoing monitoring of the security environment to identify potential threats or vulnerabilities that could compromise sensitive data.
Third-party Assessments
Organizations that use third-party vendors or service providers must ensure that those vendors or providers also meet HITRUST requirements and undergo regular assessments.
Updates to the HITRUST Framework
HITRUST updates its framework to reflect changes in regulations, technology, and security best practices. To remain in compliance, organizations must keep up with these changes and adjust security controls and policies accordingly.
If you fail to maintain your certification, it could result in the suspension or revocation of your certification, fines, and other penalties. For any organizations you do business with, losing that certification could signal that you are not committed to information security, and it may negatively impact relationships with customers and partners as well as third parties.
08. Secure Sensitive Data and Grow Your Business
HITRUST certification helps you protect the sensitive healthcare information that is the lifeblood of your business, enabling you to better deter cyber threats and prevent data breaches. While achieving HITRUST certification requires an investment of time and resources, it also provides a competitive edge in the marketplace and demonstrates your organization's commitment to data privacy and security. A few final suggestions to help you move to the next step:
-
Speak with a HITRUST assessor or consultant: If you’re not sure whether HITRUST is right for you, these experienced professionals can help you make the right decision.
-
Choose the right level: Keep in mind that there are three HITRUST certification levels — choose the one that makes the most sense for your business. Each certification nests into the next one, so you can start smaller and work your way up. You can take this quiz to find out which assessment is right for your organization!
- Focus on the right controls: The HITRUST CSF is a comprehensive framework, but not all of the controls are equally important for every organization. Focus on the controls relevant for your organization and industry.
- Use technology: There are solutions that can help you implement and maintain the HITRUST CSF by automating tasks, tracking progress, and identifying gaps in compliance. Learn more..
- Get involved: The HITRUST community is an excellent resource for digital health startups. Join forums, attend webinars, ask questions, and read resources to learn more about the HITRUST CSF.
Appendix
Sources used in this eBook, as well as additional resources for readers seeking more information on HITRUST certification.
AICPA https://www.aicpa-cima.com/
GDPR compliance https://gdpr.eu/
Health Insurance Portability and Accountability Act of 1996 | ASPE https://aspe.hhs.gov/reports/health-insurance-portability-accountability-act-1996
HITECH Act Enforcement Interim Final Rule | HHS.gov https://www.hhs.gov/hipaa/for-professionals/special-topics/hitech-act-enforcement-interim-final-rule/index.html
HIPAA Compliance Checklist 2023 https://www.hipaajournal.com/hipaa-compliance-checklist/
HITRUST Alliance https://hitrustalliance.net/
HITRUST CSF + Certification https://hitrustalliance.net/certification/hitrust-csf/
The International Information System Security Certification Consortium or (ISC)² https://www.isc2.org/
ISO/IEC 27001:2005(en), Information technology — Security techniques — Information security management systems — Requirements https://www.iso.org/obp/ui/#iso:std:iso-iec:27001:ed-1:v1:en
ISO/IEC 27002:2005 - Information technology — Security techniques https://www.iso.org/standard/50297.html
National Institute of Standards and Technology (NIST) https://www.nist.gov/
Office for Civil Rights (OCR) https://www.hhs.gov/ocr/index.html






